
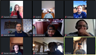
What a videoconference looks like when all participants have their cameras off. The possibility of human interaction is severely restricted.
This exploration of conversational narcissism began with "Self-Importance and Conversational Narcissism at Work: I," Point Lookout for October 4, 2023, with some definitions and examples. Briefly, conversational narcissism is the set of behaviors a conversation participant uses to direct the focus of a conversation from the topic at hand onto that participant or along directions favored by that participant. Conversational narcissism is a threat to organizational wellbeing because it distorts the outcomes of discussions, biasing them in ways preferred by individuals whose personal agendas might not align with organizational interests.
As noted in earlier posts, the methods of conversational narcissism can be categorized as emphasizing some combination of self-importance, exploitation of others, exhibitionism, and impersonal relationships. This post continues an exploration of the narcissistic behaviors that are most closely associated with impersonal relationships.
A bit of terminology
Following the pattern of previous posts in this series, I begin with some introductory information, repeated here for convenience. If you recall those earlier posts well enough, you can skip this next bit.
In the first post of this series I introduced the term abuser as a shorthand for narcissistic conversation participant, because the term narcissist won't do — not all abusers are narcissists. In general, it's the behavior that's narcissistic, not the person exhibiting the behavior (though some who exhibit the behavior are narcissists).
In these posts, I describe someone as "having the talking stick" if the conversation participants acknowledge them as the current speaker. (The term speaker won't do, because someone else might be speaking too.)
Six patterns of conversational narcissism that are associated with impersonal relationships
Guided Conversational narcissism threatens organizational
wellbeing because it biases conversations in
ways preferred by individuals, and which might
not align with organizational interestsby the work of Vangelisti, et al., I've collected 17 different patterns abusers use and which are associated with impersonal relationships. [Vangelisti 1990] Although they use the term impersonal relationships to refer to this theme, I prefer off-putting interactions. My preference arises from my desire that the term cover interactions between people who don't have much of a relationship beyond the incident at hand. This might occur, for example, in the (relatively common) case of a cross-functional team or task force comprised of people who work together only rarely. Another example: making a case to a governance panel for a waiver of policy.
In the previous post I described five patterns abusers employ to create distractions that insert distance between themselves and other participants. In this post I examine — briefly — the use of cameras in videoconferences, and then explore how abusers handle and use questions.
- Camera off in videoconferences
- Videoconferencing is increasingly common these days, even for teams whose members are all or almost all co-located. Partly driven by work-from-home, and partly by chaotic travel schedules, videoconferencing is the way of things now. In the context of conversational narcissism, videoconferencing compels us to address the question of camera usage. Shall we require cameras to be enabled? Shall we require live, full-motion views of every meeting participant? (Aside: These last two sentences are examples of rhetorical questions. See below.)
- Abusers recognize the power of turning off their cameras. Out of sight of the participants, abusers are free to engage in text messaging conversations with anyone, including other participants. And "camera-off" communicates a message of, "I'm too important for the drivel of this conversation. I'll attend this meeting live if it turns to topics that matter." When abusers want to, they can activate their cameras and join the meeting. And when they do that, other participants take notice and await the abuser's next pronouncement.
- Nevertheless, adopting a cameras-on policy carries risks. Unless you're prepared to enforce the policy, abusers who defy the policy will be able to create with their defiance even more distance between themselves and other participants.
- Using questions as tools of detachment
- We generally regard questions as honest requests for insight or information. Most questions actually are tools of enlightenment. For abusers, though, questions serve another purpose. They separate abusers from everyone else. Separation is accomplished in a variety of ways, but let me describe just one.
- Suppose the conversation is about to enter the domain of another participant — someone whom the abuser regards as a competitor for attention. A well-timed question about a different, unrelated topic can prevent the conversation from entering the competitor's domain. And if the topic of the question is in the abuser's "wheelhouse," the question serves to bring the conversation into territory where the abuser is dominant.
- Asking themselves questions aloud and answering them
- This figure of speech is an old one. It has a Greek name: hypophora. Perhaps an illustration will explain it best: "Have I ever seen this technique in use in a real meeting? Yes, of course. Does it actually work for abusers? Well, it's most likely to work if the other participants haven't yet given it a name or recognized it. Are there no other reasons why it works? There are, indeed — the other participants let it work."
- Avoiding questions that lead away
- If someone asks the abuser a question, and the answer leads along a path the abuser would rather not follow, the abuser balks. Several strategies will serve the abuser's purpose: (a) Interpret the question in a way that avoids the disfavored path; (b) Duck the question with a plausible yet meaningless excuse such as, "We'll have to see," or, "We're looking into that but I can't say much at this point," or, "Intriguing possibility, of course, but it's too early to say;" (c) Ask himself or herself a question, answer it, then move to a new topic. See "Asking themselves questions aloud and answering them."
- Asking questions that are off topic
- Asking off-topic questions does derail the conversation. But the skilled abuser crafts questions that redirect the conversation along a path the abuser prefers. An example of such a path is one that leads the group to appreciate more fully the abuser's true talents.
- Abusers avoid asking — or indeed, they avoid even entertaining — questions that lead the group to appreciate anyone else, or to explore any topic the abuser would rather not see explored. One example: clarifying questions. The abuser rarely asks questions that clarify ambiguous points, unless the issue relates to some aspect of the abuser's agenda.
- Asking rhetorical questions
- Although the rhetorical question is a legitimate question in the grammatical sense, its function is not interrogatory. Usually, the rhetorical question is a device for making a point in an interesting way. It serves to compel auditors to silently devise answers, and in so doing, it commands their attention. The rhetorical question is thus a device almost designed for the abuser.
- Abusers can use rhetorical questions to direct the thoughts of auditors along the lines abusers prefer. Having accomplished that feat, the abuser can then show the auditors the next step using another rhetorical question, or any other suitable device. In effect, the rhetorical question mitigates the risk of losing the talking stick after making one's point.
Last words
Over the course of these nine posts, I might have left the impression that I regard the abuser as someone who intentionally and for evil purposes employs the tactics I've identified. That does occur. I've witnessed it myself. But I suspect that most examples of these tactics in the wild occur outside the awareness of the people who use them. In most cases, I believe (without evidence) that the behaviors in question are associated with habits of long standing. And they can be replaced by new habits that are more constructive for all concerned.
This series has explored a variety of tactics available to any participant in any conversation. My focus has been the kind of conversation that occurs in meetings at work. Although I have described over 50 such tactics, I'm certain there are many more. Two paths open from this point for further work. One is elaboration of the set of tactics so far included to describe them in greater detail, and to include other tactics where possible. A second and more important path is a collection of responses to the tactics identified. The most effective defense against conversational narcissism is for participants in workplace conversations to be prepared to deal with these tactics in the moment. In workplaces so prepared, abusers are more likely to be deterred. And that is the most effective response.
If you recognize some of these tactics and would like my thoughts about effective responses, contact me: rbrenaXXxGCwVgbgLZDuRner@ChacDjdMAATPdDNJnrSwoCanyon.com. ![]() First issue in this series
First issue in this series ![]() Top
Top ![]() Next Issue
Next Issue
Is every other day a tense, anxious, angry misery as you watch people around you, who couldn't even think their way through a game of Jacks, win at workplace politics and steal the credit and glory for just about everyone's best work including yours? Read 303 Secrets of Workplace Politics, filled with tips and techniques for succeeding in workplace politics. More info
Footnotes
Your comments are welcome
Would you like to see your comments posted here? rbrenaXXxGCwVgbgLZDuRner@ChacDjdMAATPdDNJnrSwoCanyon.comSend me your comments by email, or by Web form.About Point Lookout
 Thank you for reading this article. I hope you enjoyed it and
found it useful, and that you'll consider recommending it to a friend.
Thank you for reading this article. I hope you enjoyed it and
found it useful, and that you'll consider recommending it to a friend.
This article in its entirety was written by a human being. No machine intelligence was involved in any way.
Point Lookout is a free weekly email newsletter. Browse the archive of past issues. Subscribe for free.
Support Point Lookout by joining the Friends of Point Lookout, as an individual or as an organization.
Do you face a complex interpersonal situation? Send it in, anonymously if you like, and I'll give you my two cents.
Related articles
More articles on Effective Meetings:
 Misleading Vividness
Misleading Vividness- Group decision making usually entails discussion. When contributions to that discussion include vivid
examples, illustrations, or stories, the group can be at risk of making a mistaken decision.
 Interrupting Others in Meetings Safely: III
Interrupting Others in Meetings Safely: III- When we need to interrupt someone who's speaking in a meeting, we risk giving offense. Still, there
are times when interrupting is in everyone's best interest. Here are some more techniques for interrupting
in situations not addressed by the meeting's formal process.
 Barriers to Accepting Truth: I
Barriers to Accepting Truth: I- In workplace debates, a widely used strategy involves informing the group of facts or truths of which
some participants seem to be unaware. Often, this strategy is ineffective for reasons unrelated to the
credibility of the person offering the information. Why does this happen?
 Newly Virtual Politics: Meetings
Newly Virtual Politics: Meetings- Pandemic or not, workplace politics marches on. But with the pandemic and the prevalence of formerly
co-located teams becoming more virtual, workplace politics takes a new form, especially clearly so in
meetings.
 Pre-Decision Discussions: Reasoning
Pre-Decision Discussions: Reasoning- When we meet to resolve issues related to upcoming decisions, we sometimes rely on reasoning to help
find solutions. Contributions to these discussions generally use mixtures of deductive, inductive, and
abductive reasoning. How do they differ, and what are their strengths and risks?
See also Effective Meetings for more related articles.
Forthcoming issues of Point Lookout
 Coming October 1: On the Risks of Obscuring Ignorance
Coming October 1: On the Risks of Obscuring Ignorance- A common dilemma in knowledge-based organizations: ask for an explanation, or "fake it" until you can somehow figure it out. The choice between admitting your own ignorance or obscuring it can be a difficult one. It has consequences for both the choice-maker and the organization. Available here and by RSS on October 1.
 And on October 8: Responding to Workplace Bullying
And on October 8: Responding to Workplace Bullying- Effective responses to bullying sometimes include "pushback tactics" that can deter perpetrators from further bullying. Because perpetrators use some of these same tactics, some people have difficulty employing them. But the need is real. Pushing back works. Available here and by RSS on October 8.
Coaching services
I offer email and telephone coaching at both corporate and individual rates. Contact Rick for details at rbrenaXXxGCwVgbgLZDuRner@ChacDjdMAATPdDNJnrSwoCanyon.com or (650) 787-6475, or toll-free in the continental US at (866) 378-5470.
Get the ebook!
Past issues of Point Lookout are available in six ebooks:
- Get 2001-2 in Geese Don't Land on Twigs (PDF, )
- Get 2003-4 in Why Dogs Wag (PDF, )
- Get 2005-6 in Loopy Things We Do (PDF, )
- Get 2007-8 in Things We Believe That Maybe Aren't So True (PDF, )
- Get 2009-10 in The Questions Not Asked (PDF, )
- Get all of the first twelve years (2001-2012) in The Collected Issues of Point Lookout (PDF, )
Are you a writer, editor or publisher on deadline? Are you looking for an article that will get people talking and get compliments flying your way? You can have 500-1000 words in your inbox in one hour. License any article from this Web site. More info
Follow Rick
Recommend this issue to a friend
Send an email message to a friend
rbrenaXXxGCwVgbgLZDuRner@ChacDjdMAATPdDNJnrSwoCanyon.comSend a message to Rick
![]() A Tip A Day feed
A Tip A Day feed
![]() Point Lookout weekly feed
Point Lookout weekly feed
 My blog, Technical Debt for Policymakers, offers
resources, insights, and conversations of interest to policymakers who are concerned with managing
technical debt within their organizations. Get the millstone of technical debt off the neck of your
organization!
My blog, Technical Debt for Policymakers, offers
resources, insights, and conversations of interest to policymakers who are concerned with managing
technical debt within their organizations. Get the millstone of technical debt off the neck of your
organization!